Secrets
A secret is a container of key/value pairs. The key as well as the value are always strings. Secrets are stored encrypted in the database. The type of encryption as well as group and flow restrictions determine who can access the secret. Secrets can be used to store e.g. passwords, API keys and other sensitive information.
The list of secrets can be found under the Secrets tab in the main menu. Here you can also see the encryption type of the secret and whether is valid still.
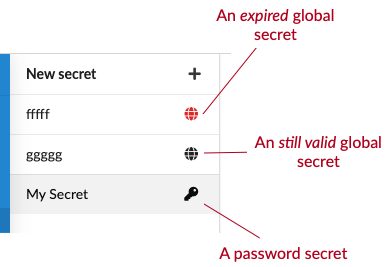
The encryption types are as follows:
Global encryption
The secret is encrypted using a global key. This means that all Manatee instances can decrypt the secret.
Local machine encryption
The secret is encrypted using a machine key. This means that only Manatee instances on the same machine can decrypt the secret. In order to encrypt a secret using a machine key you need to specify the machine name and the Conductor must be running and have access to the machine.
Local user encryption
The secret is encrypted using a user key. This means that only the user who created the secret can decrypt it. In order to encrypt a secret using a user key you need to specify the user name and the Conductor must be running and have access to the machine on which the user is logged in.
Password based encryption
The secret is encrypted using a password. This means that only users who know the password can decrypt the secret.
Secret editor
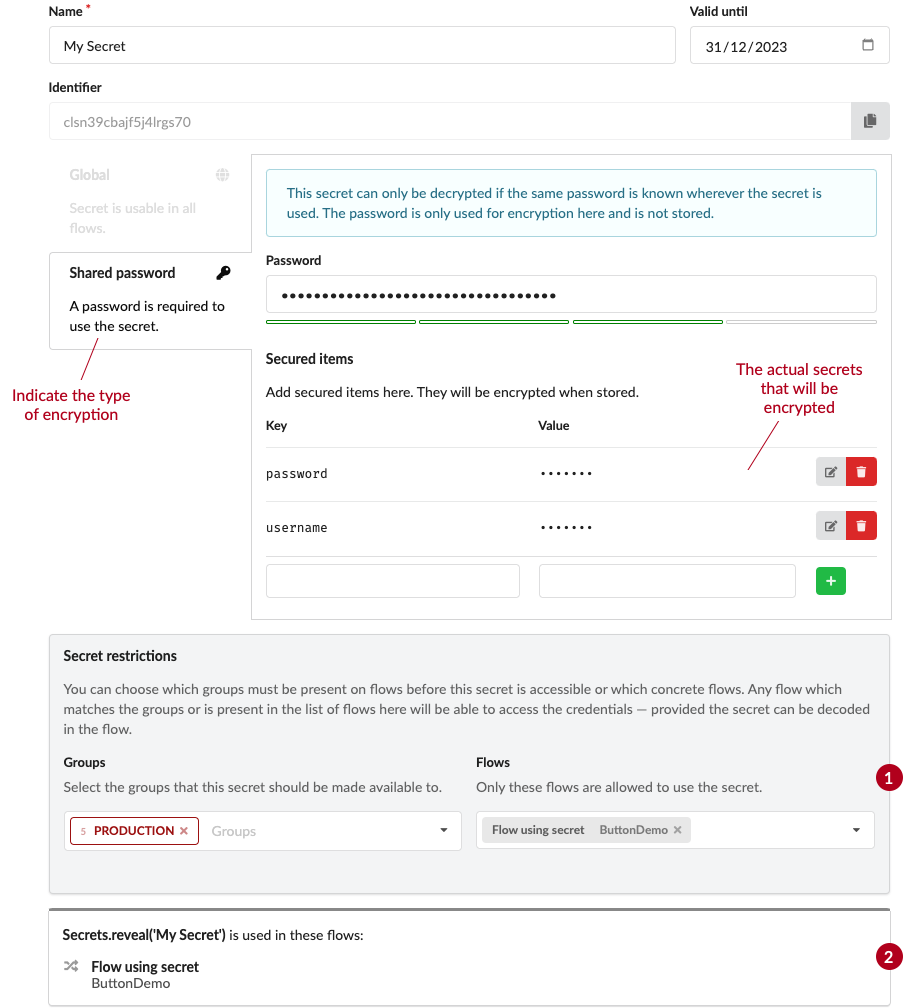
The main UI for secrets is the secret editor. Here you can edit the name, description and encryption type of the secret as well as add, edit and remove key/value pairs.
It is also possible to specify a valid until date for the secret. If this date is set the secret cannot be used after this date. This is useful for e.g. API keys that have a limited lifetime or for passwords that need to be changed regularly.
Restrictions on secrets
The encryption type of the secret determines who can access the secret. In addition to this you can also add restrictions to the secret. This is useful if you want to restrict the use of a secret to a specific flow or specific groups.
(1) in the image above shows the restrictions for the secret.
If you only specify groups only machines where the primary and at least one secondary group is matched.
If you only specify flows then only these flows will be able to access the secret.
If you specify both groups and flows then either the groups must match or the flows must match.
Usages of secrets
(2) in the image above shows the usages of the secret. Here you can see which flows are using the secret and jump directly to where the secret is used.
